Secure Data Operations & Compliance Integrity
We prioritize security, privacy, and transparency at every level of our product and operations. Our platform is built to exceed industry standards like SOC 2 Type 2, HIPAA, GDPR, and CCPA – so your data stays protected and compliant.
Secure Data Transmission
Protecting all data in motion with secure, encrypted communication across every connection.
-
Secure Data in Transit
All information exchanged between Graphio, customers, and external services is protected using TLS 1.2/1.3 encryption. This ensures that sensitive data cannot be intercepted or altered during transmission.
-

Encrypted Communication Between Services
Every internal microservice within Graphio’s infrastructure communicates via encrypted TLS/SSL channels, eliminating exposure of sensitive data inside private networks.
-

Strict HTTPS Enforcement
Graphio APIs and web interfaces enforce HTTPS-only access, blocking any unsecured HTTP requests to prevent man-in-the-middle or downgrade attacks.
Privacy Assurance
-
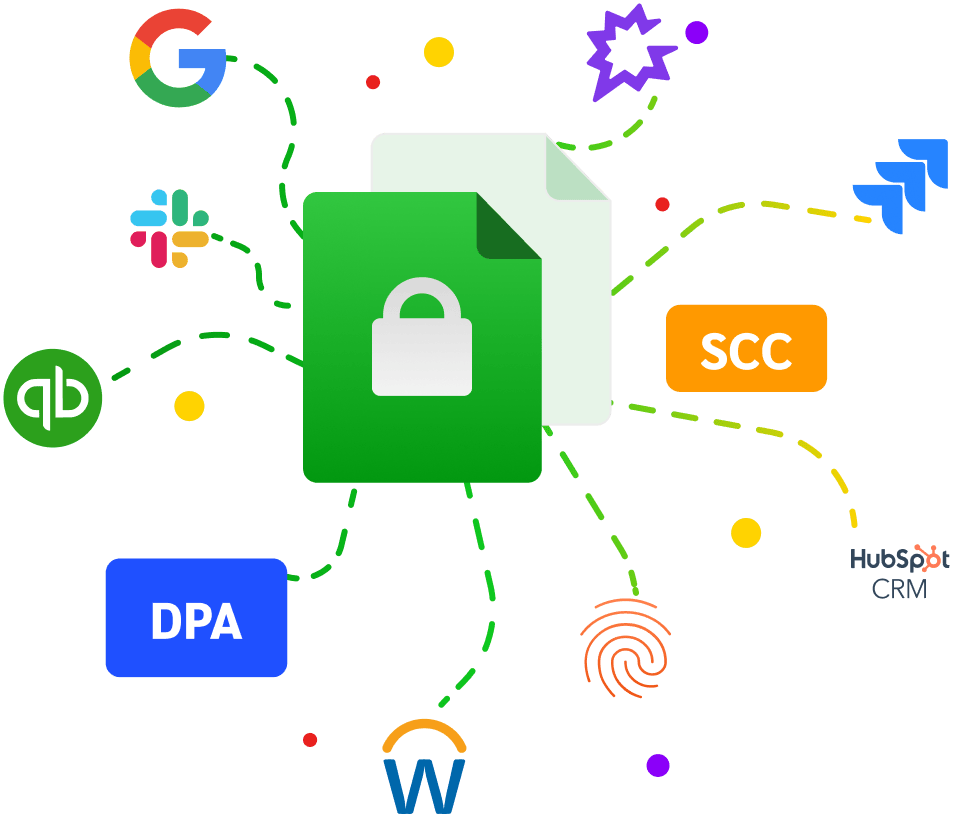
Metadata-Only Processing
Graphio processes only metadata — such as timestamps, source identifiers, and event categories — without ever accessing or analyzing the actual content of messages, files, or emails.
-
No Content Inspection or Retention
Raw data obtained from external APIs (Slack, Jira, HubSpot, Google Workspace, QuickBooks, and others) is used solely to generate metadata packets, which are immediately processed and securely deleted after completion.
-
Minimal Access Principle (Least Privilege)
All internal services and employees operate under the least-privilege access model, ensuring that every component and user has only the minimal permissions required to perform its function.
-
Regulatory Alignment
Data processing complies with Data Processing Addendum (DPA) and Standard Contractual Clauses (SCC), ensuring full legal protection for international data transfers and enterprise clients.
Data Storage Security
Encrypted, isolated data storage with continuous monitoring and protection.
-
Encrypted Databases
All databases are stored on AES-256–encrypted volumes to prevent unauthorized access in the unlikely event of a system breach.
-

Field-Level Encryption for Sensitive Data
Any personally identifiable information (PII), such as employee names, email addresses, or user IDs, is encrypted at the database field level — ensuring additional protection even within the database layer itself.
-
Isolated Backup Storage
Backups are encrypted and stored separately in restricted-access environments, isolated from production systems. Access to backup data is limited to senior security administrators under strict audit control.
-
Regular Penetration Testing
Graphio conducts periodic penetration tests and vulnerability assessments to identify potential weaknesses in its storage and encryption mechanisms.
Compliance Assurance

-
SOC 2 Type 2 Compliant
Graphio’s security controls are independently audited under the SOC 2 Type 2 framework, covering operational effectiveness of data protection, confidentiality, and availability controls.
-
HIPAA Compliant
Our systems meet HIPAA security and privacy rules, ensuring protection for health-related data when applicable.
-
GDPR & CCPA Compliance
Graphio is compliant with EU General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA), enabling full transparency and user control over personal data. Users can request data deletion or export at any time.
-
GDPA & SCC Frameworks
We maintain and sign Data Processing Agreements (DPAs) and Standard Contractual Clauses (SCCs) with all enterprise clients and subprocessors to ensure legal compliance for international data transfers.
Infrastructure Access Governance
Data Lifecycle Policy
Minimal retention, secure disposal, full customer control of stored data.
-
Limited Retention Periods
Temporary data, cache, and logs are retained for no longer than 30 days and then automatically purged from all systems.
-
Immediate Data Deletion Upon Revocation
Users can revoke access and delete all stored data by removing the Graphio integration from connected systems such as Google Workspace, Slack, HubSpot, etc.
-
Secure Backup Disposal
All encrypted backups are automatically destroyed upon expiration of their retention window, preventing residual data recovery.
-
User-Controlled Privacy
Graphio provides clear interfaces and documentation for customers to manage, audit, and erase their data at any time in compliance with GDPR Article 17 (“Right to be Forgotten”).
Platform Enablement Framework
-
Fast and Secure Setup
Implementing Graphio takes only a few days. The onboarding process follows secure deployment and authentication standards to ensure compliance from the first connection.
-
No Developers or Coding Required
All integrations are plug-and-play — requiring no engineering effort, code deployment, or manual key exchange. This minimizes security risks during setup.
-
Pre-Verified Connectors
Every integration (Slack, HubSpot, Jira, Google Workspace, QuickBooks, etc.) passes Graphio’s internal security and privacy review before being enabled in production environments.
-
Automated Configuration Audits
The platform continuously monitors integration states and permissions, alerting administrators if scopes or security settings change.